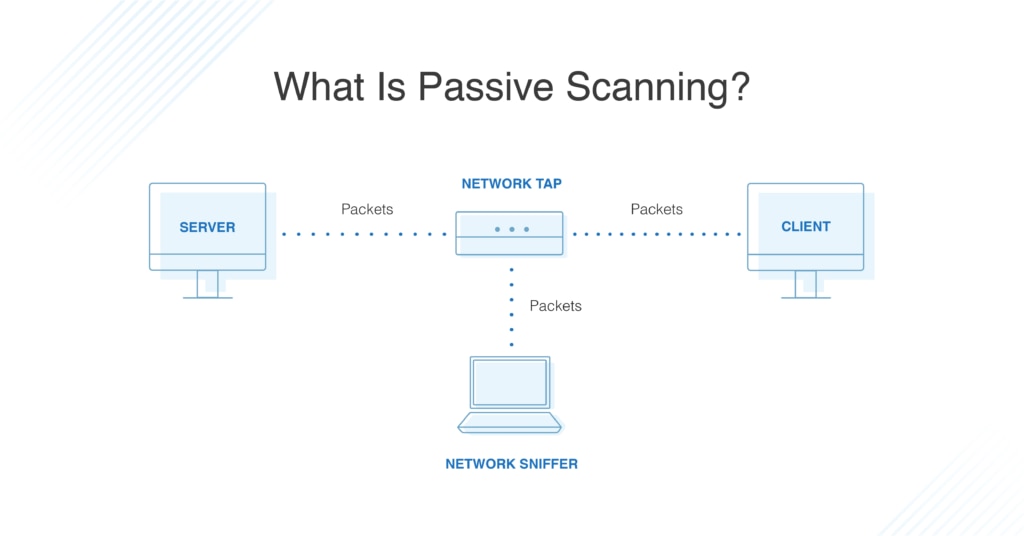
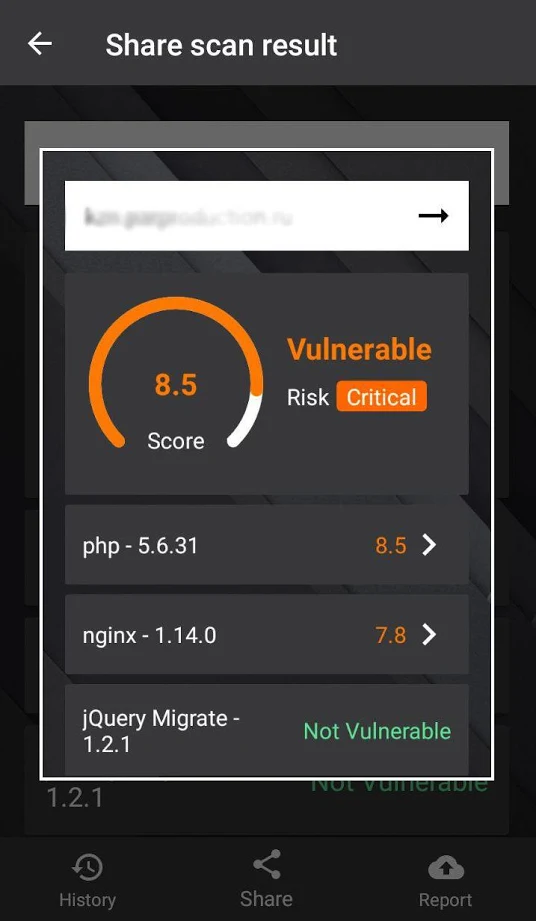
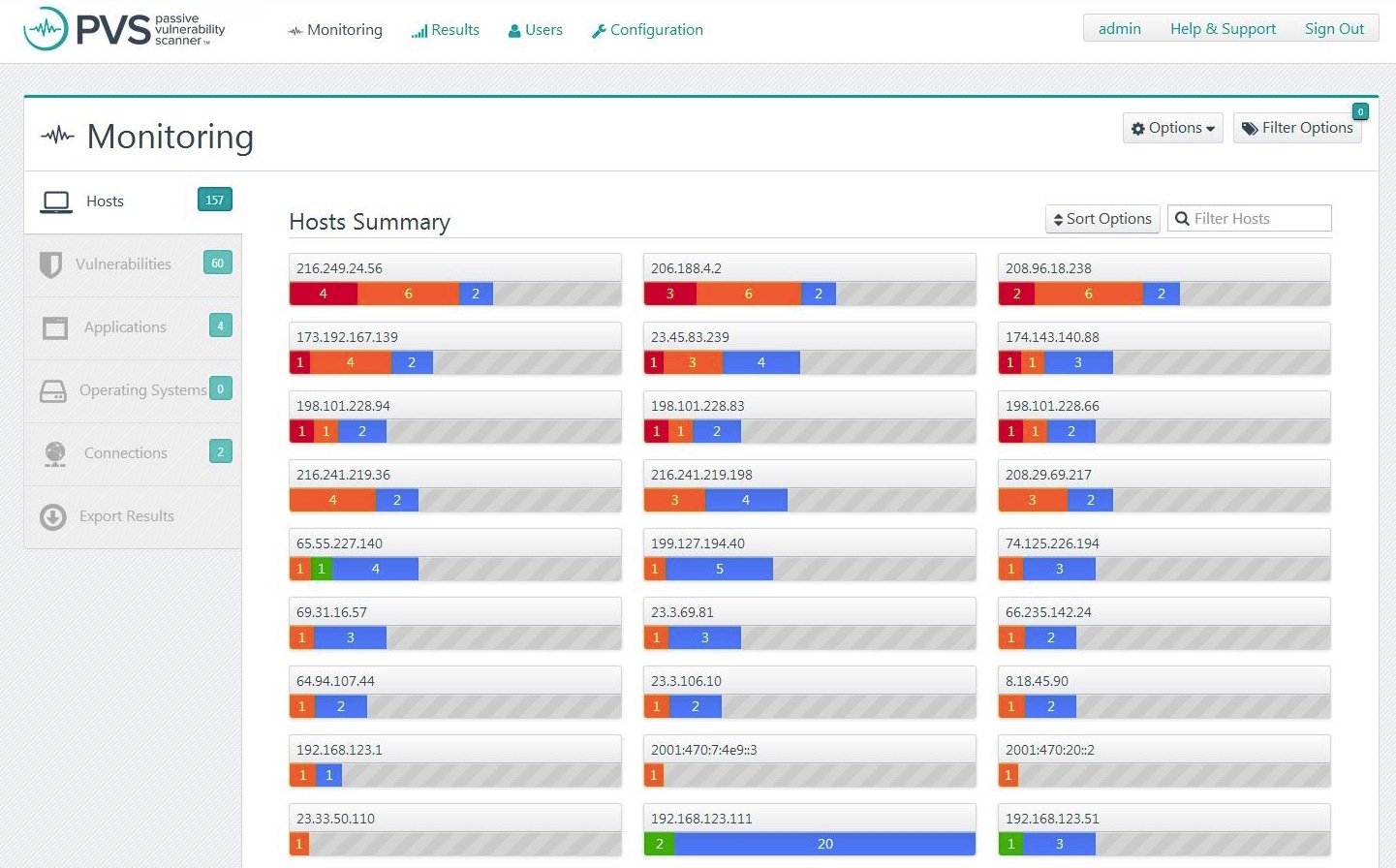
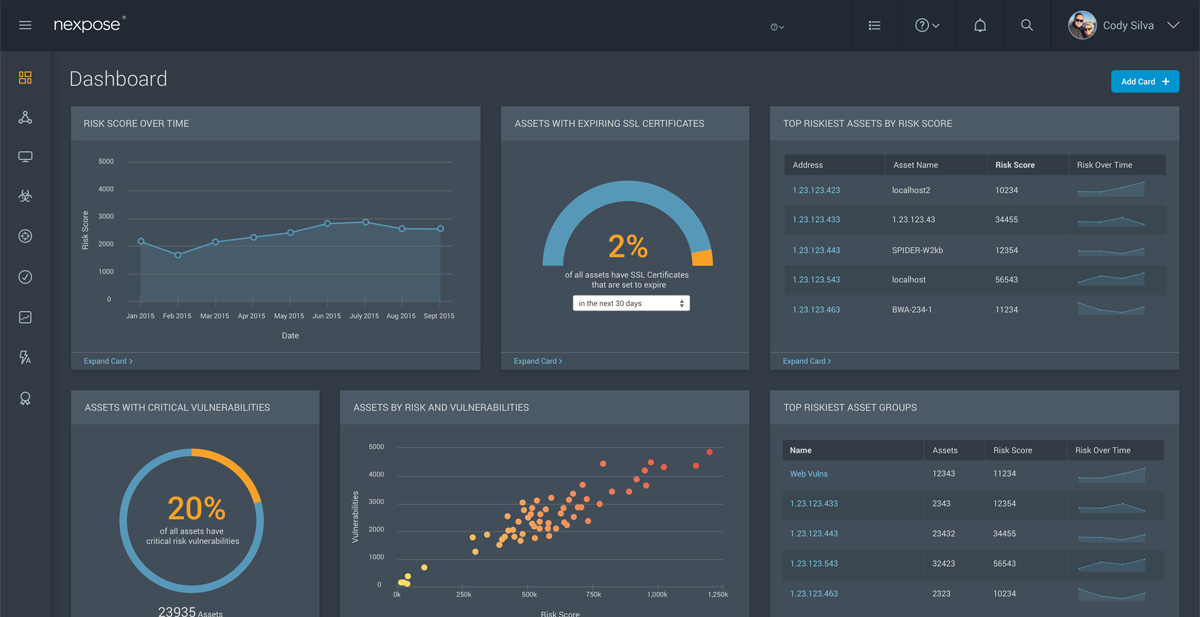
Passive Vulnerability Scanner Enterprise - subscription license (1 year) - 10 GB capacity - SERV-PVS-ENT-10GB - Vulnerability - CDW.com
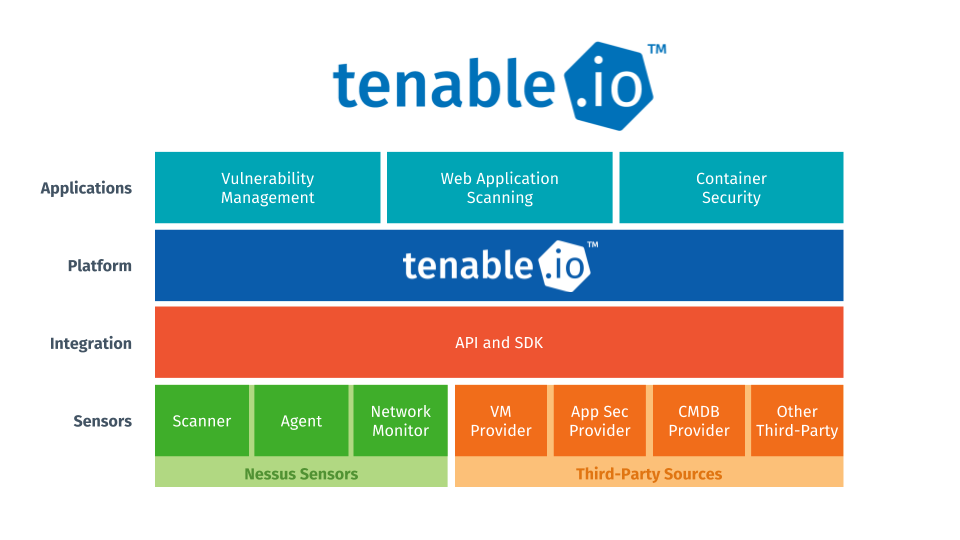
Tenable Delivers the First Vulnerability Management Platform to Unify IT and OT Security - IT Security Guru